The Red Team Arsenal: 5 Cutting-Edge Tools for Hardware Hackers and Ethical Hackers
While blue teams defend, red teams attack. They share a common goal, however – help identify and address gaps in organizations’ defenses before these weaknesses can be exploited by malicious actors. The blue/red team exercises provide invaluable insights across the technical, procedural and human sides of security and can ultimately help organizations fend off actual attacks.
We recently explored open-source tools that blue teams use to defend against simulated attacks and highlighted gadgets that could cause security trouble in the wrong hands. This time, we’ll dive into five cutting-edge, compact tools that hobbyist hardware hackers, red teamers, and ethical hackers can wield while honing their skills or performing their job.
1. Raspberry Pi 5
The Raspberry Pi has become a favored tool among security professionals, students, and enthusiasts. This affordable single-board computer can be loaded with penetration testing tools, serving multiple roles such as network sniffing, automated security testing, and IoT device analysis.

The Raspberry Pi supports various operating systems tailored for different purposes, making it ideal for penetration testing and security auditing. Additionally, several interesting tools and projects leverage the Raspberry Pi as the hardware platform.
2. HackRF One
The HackRF One is a powerful tool for exploring radio frequencies, allowing users to transmit and receive signals from 1 MHz to 6 GHz. This compact device can experiment with various wireless communications, making it a versatile tool for security professionals and RF enthusiasts.

With HackRF One, you can assess wireless systems, perform replay attacks, and explore IoT device vulnerabilities.
3. WiFi Pineapple
The WiFi Pineapple is a sleek gadget that probes the security of wireless networks by simulating a conventional access point. It comes with a custom operating system tailored for wireless penetration testing and provides a stable environment for complex security assessments.

The WiFi Pineapple can perform various attacks to identify vulnerabilities in wireless networks.
4. Deauther Watch
The Deauther Watch disrupts Wi-Fi connections by sending deauthentication packets, making it a handy tool for Wi-Fi security testing. It also features Wi-Fi scanning, monitoring, and packet capturing capabilities.

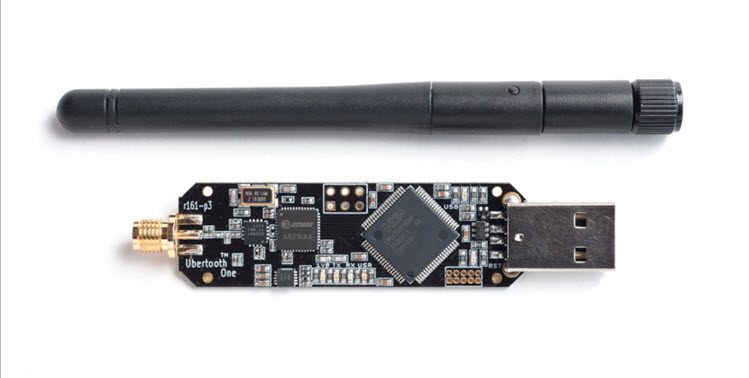
5. Ubertooth One
The Ubertooth One is designed for monitoring Bluetooth communications and analyzing Bluetooth packets. This versatile gadget supports various security testing scenarios and can be customized to meet specific needs.
Conclusion
These cutting-edge tools offer incredible capabilities for hardware hackers and ethical hackers alike. However, ethical considerations are crucial, and users must obtain permission before using these tools in any environment. Organizations should implement measures to protect against unauthorized use of these devices on their networks. With the right knowledge and approach, these tools can help enhance security practices and stay ahead of potential threats.


