The Rise of Sophisticated Mobile Phishing Techniques
A recently discovered sophisticated mobile phishing technique has been observed in financial fraud campaigns across the Czech Republic, Hungary, and Georgia. This phishing method leverages progressive web applications (PWA), offering a native-app-like experience and gaining momentum on both Android and iOS devices.
What makes this technique standout is its ability to install a phishing application from a third-party website without the user having to allow third-party app installation, as detected by cybersecurity firm ESET.
Decoding PWA Phishing on iOS and Android
This new phishing technique capitalizes on the way PWAs work, bypassing the need for users to allow third-party installations. On iOS, phishing websites mimic well-known applications’ landing pages and prompt victims to add a PWA to their home screens, creating a seamless experience.
Meanwhile, on Android devices, the PWA is installed through custom pop-ups in the browser, leading to the silent installation of a web Android Package Kit (WebAPK). These WebAPKs appear as native Android applications, further blurring the lines between legitimate apps and phishing attempts.
The discovery of this technique was first highlighted by CSIRT KNF in July 2023, shedding light on the evolving landscape of mobile phishing.
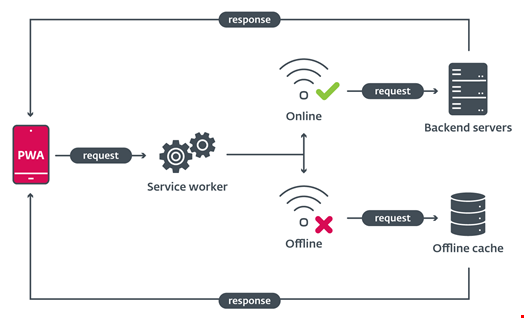
ESET’s findings revealed mobile phishing campaigns targeting banks in the Czech Republic, Hungary, and Georgia in November 2023. These campaigns utilized various delivery mechanisms, including voice calls, SMS messages, and malvertising, to lure victims into installing malicious apps under the guise of legitimate banking updates.
It was discovered that two distinct threat actors were behind these campaigns, further showcasing the complexity and organization of modern phishing operations.
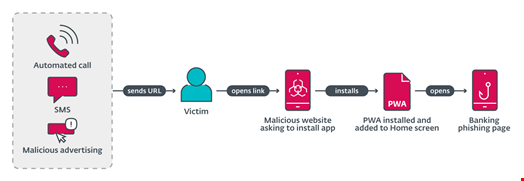
ESET’s proactive approach in notifying the targeted banks underscores the importance of collaboration between cybersecurity experts and financial institutions in combating sophisticated cyber threats.
To learn more about emerging cyber threats and social engineering tactics, explore our article on Top Social Engineering Techniques.


