
The Iranian state-backed hacking outfit known as APT42 has been employing sophisticated social engineering tactics to breach target networks and cloud environments.
According to a report by Google Cloud subsidiary Mandiant, the targets of these attacks include various organizations such as Western and Middle Eastern NGOs, media outlets, academic institutions, legal services, and activists.
The company stated that “APT42 has been seen posing as journalists and event organizers to establish trust with their targets through ongoing communication, and then using this trust to deliver malicious content or documents.”
This elaborate social engineering technique has allowed APT42 to obtain credentials and gain initial access to cloud environments for data exfiltration operations of strategic interest to Iran.
APT42, also known as Damselfly and UNC788, was first identified by Mandiant in September 2022 as an Iranian state-sponsored cyber espionage group focused on gathering information for the Iranian government.
It is believed to be part of another well-known group, APT35, which is associated with Iran’s Islamic Revolutionary Guard Corps (IRGC) and operates with different objectives.
While APT35 concentrates on long-term malware attacks targeting U.S. and Middle Eastern organizations, APT42 specifically targets individuals and entities to serve the Iranian regime’s domestic and foreign policy goals.
In earlier campaigns, Charming Kitten, a part of APT35, targeted high-profile individuals involved in Middle Eastern affairs, highlighting the group’s focus on data theft through phishing tactics.
The attacks orchestrated by these groups involve elaborate credential harvesting procedures, using spear-phishing emails with malicious links to deceive victims and harvest Microsoft, Yahoo, and Google credentials.
Alongside credential theft, the threat actors engage in data exfiltration operations within victims’ cloud infrastructure, aiming to retrieve sensitive information after establishing trust with the targets.
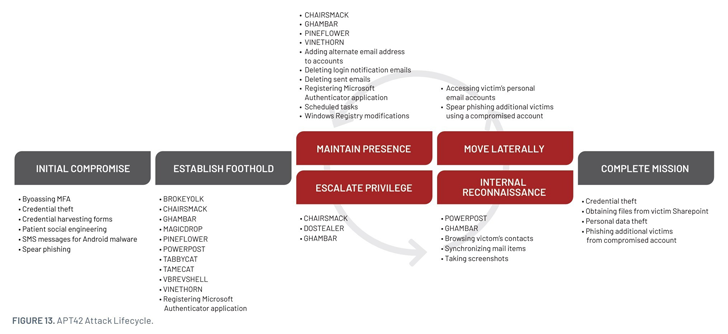
Mandiant highlighted the use of custom backdoors such as NICECURL and TAMECAT by APT42 to maintain access to compromised systems and deploy additional malware or execute malicious commands.
These tools serve as gateways for the threat actors to conduct their surveillance operations while minimizing their detection footprint.
Despite the challenging landscape for network defenders, Mandiant advises organizations to remain vigilant and continuously enhance their security posture to mitigate the evolving threats posed by APT42.
Stay connected with us on Twitter and LinkedIn for more exclusive cybersecurity content.


