The Rise of AceCryptor: Trends and Insights from H2 2023
It’s no secret that the world of cybersecurity is constantly evolving. With new threats emerging every day, it’s essential for security experts to stay ahead of the curve. In a recent blogpost, ESET shared insights from their telemetry data, shedding light on the latest trends in the world of malware.
One of the main highlights from the report is the significant increase in the usage of AceCryptor in the second half of 2023. While the first half of the year saw a steady flow of attacks, the second half witnessed a dramatic surge in AceCryptor-packed malware spreading across various European countries.
Key Points to Note:
- AceCryptor continued to be a popular choice for threat actors, packing malware families like SmokeLoader, STOP ransomware, and Vidar stealer.
- The number of attacks using AceCryptor more than doubled in H2 2023, with a particular focus on European countries.
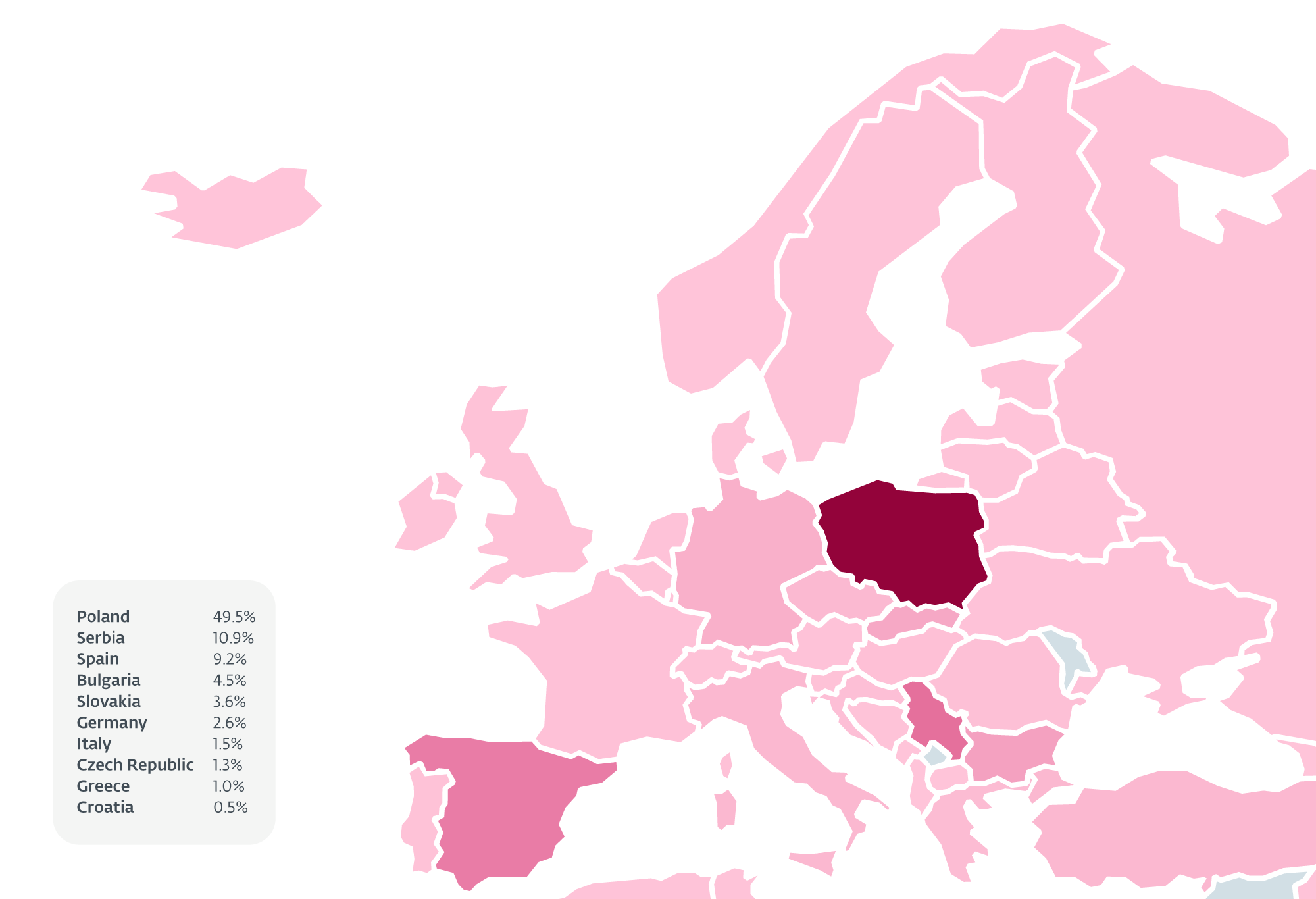
- Rescoms (Remcos) RAT emerged as a new player, leveraging AceCryptor for phishing campaigns across Poland, Serbia, Bulgaria, and Slovakia.
Insights from the Data:
With over 42,000 ESET users protected from AceCryptor threats in the second half of 2023, the severity of the situation cannot be ignored. Spam campaigns targeted at European countries saw a surge in activity, with AceCryptor being used as the initial compromise vector.
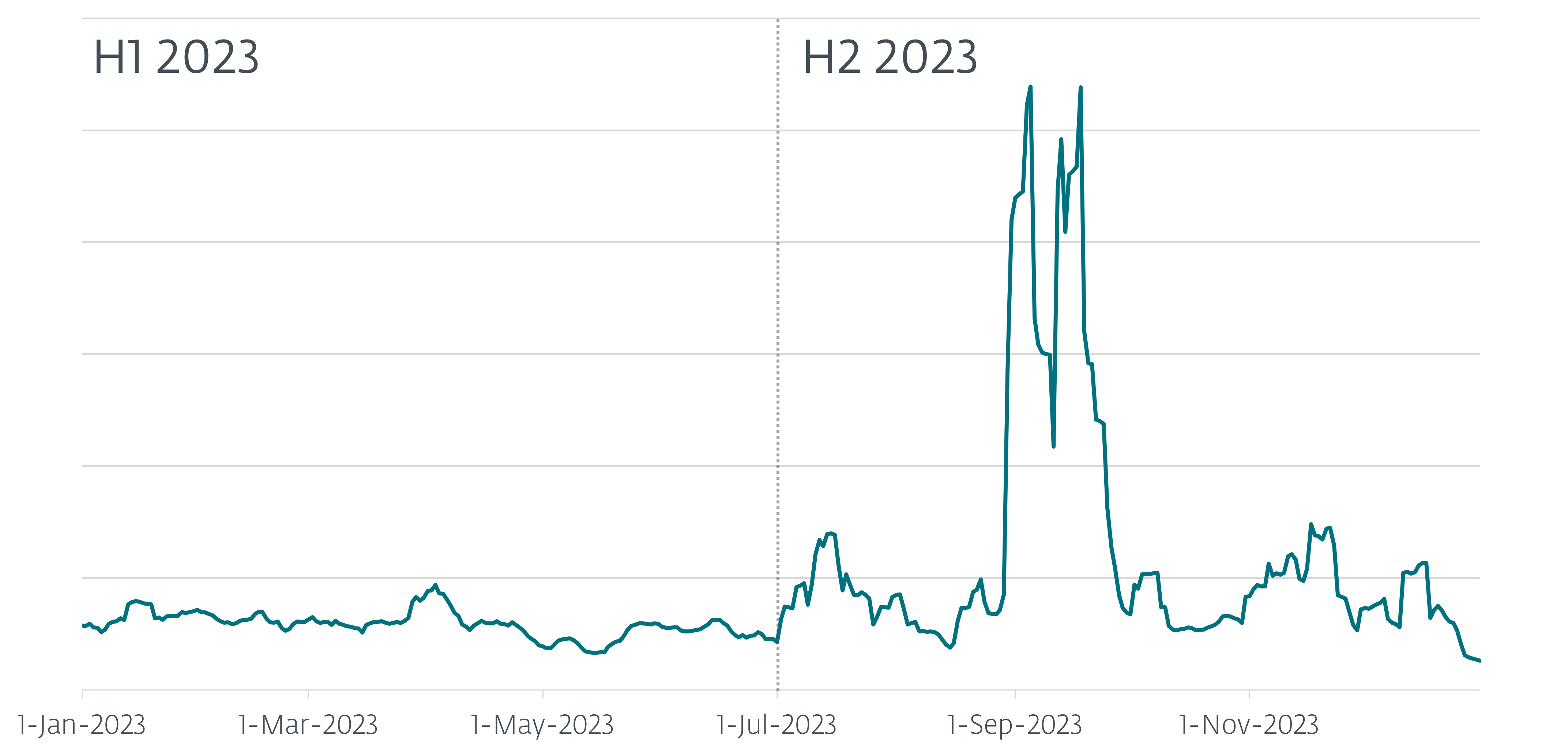
The data also revealed a shift in the malware landscape, with some popular families reducing their usage of AceCryptor. However, the rise of Rescoms and other threat actors filling the gap posed a new challenge for cybersecurity professionals.
Unveiling Rescoms Campaigns:
In the second half of 2023, Rescoms emerged as a dominant player, with over 32,000 hits registered in phishing campaigns across Poland, Serbia, Spain, Bulgaria, and Slovakia. The campaigns targeted local businesses, using deceptive tactics to lure victims into opening malicious attachments.
From sophisticated email spoofing techniques to tailored phishing messages, the campaigns displayed a high level of sophistication. Attackers leveraged compromised accounts and personalized information to increase the chances of their targets falling victim to the scam.
Protecting Against AceCryptor Attacks:
As the threat landscape continues to evolve, it’s crucial for individuals and organizations to stay vigilant. By understanding the tactics and techniques used by threat actors, security professionals can better equip themselves to defend against such attacks.
With comprehensive Indicators of Compromise (IoCs) and insights into the MITRE ATT&CK techniques employed by malicious actors, proactive mitigation strategies can be implemented to safeguard against AceCryptor and Rescoms campaigns.
For more information and insights on the latest cybersecurity trends, feel free to reach out to ESET Threat Intelligence.


