ESET Research
Discovering the Zero-Day Telegram for Android Exploit – EvilVideo Vulnerability

22 Jul 2024
•
,
6 min. read

ESET researchers have made a groundbreaking discovery – a zero-day exploit targeting Telegram for Android, named the EvilVideo vulnerability. This exploit allows attackers to send malicious payloads disguised as multimedia files via Telegram channels, groups, and chats.
We uncovered this exploit being advertised in an underground forum, prompting swift action. After analyzing and reporting the vulnerability, Telegram released a patch on July 11th, 2024, fixing the issue in versions 10.14.5 and above.
For a detailed overview and video demonstration of the EvilVideo vulnerability, check out Figure 1 below.
Figure 1. Explanation of the EvilVideo vulnerability
Key highlights of this discovery:
- An underground forum post on June 26th, 2024, revealed the zero-day exploit targeting Telegram for Android.
- The vulnerability, called EvilVideo, was promptly reported to Telegram, leading to a fix on July 11th, 2024.
- Attackers could use EvilVideo to deliver malicious payloads disguised as video files on unpatched Telegram for Android.
- The exploit is only effective on Android Telegram versions 10.14.4 and prior.
Unveiling the Discovery
We stumbled upon the exploit being sold in an underground forum, as illustrated in Figure 2.
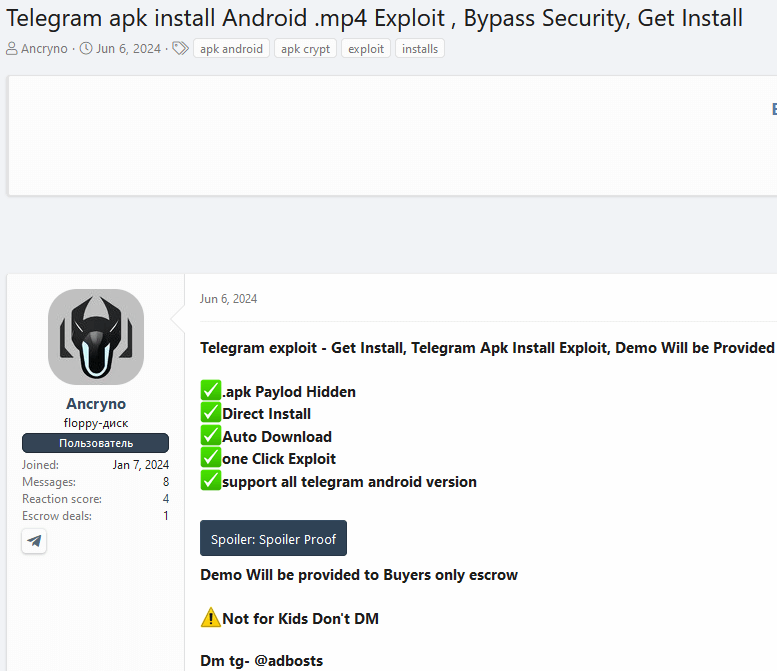
The seller showcased screenshots and a video of testing the exploit in a public Telegram channel, enabling us to acquire the payload for further examination.
Analyzing the Exploit
Our investigation uncovered that the exploit is operational on Telegram versions 10.14.4 and earlier. The payload likely exploits the Telegram API, enabling the upload of specialized multimedia files programmatically.
The exploit hinges on creating a payload that presents an Android app as a multimedia preview rather than a binary attachment. When shared in a chat, the malicious payload masquerades as a 30-second video (see Figure 3).
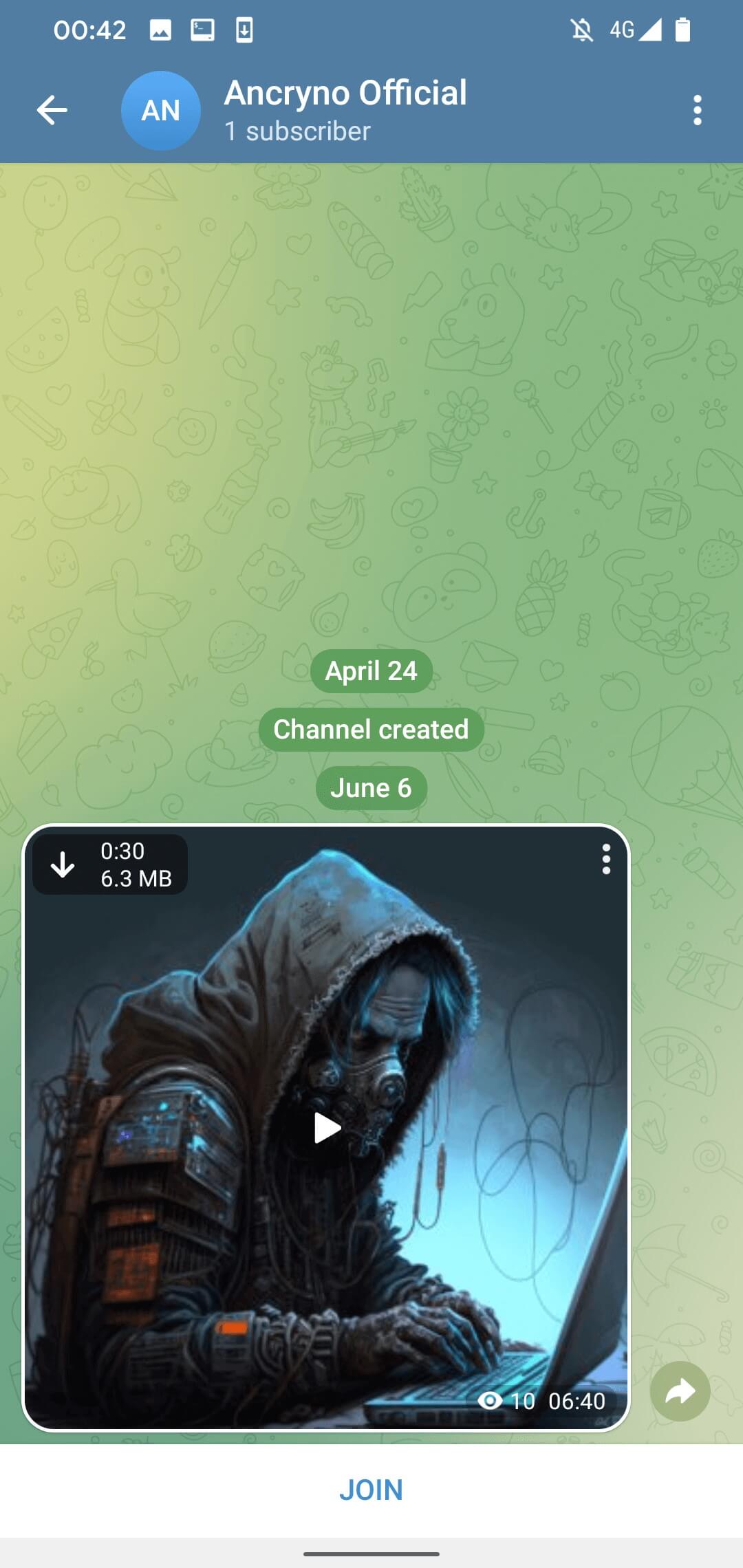
By default, media files received via Telegram automatically download. This means that if users have this option enabled, the malicious payload will download upon opening the chat where it was shared. Even if the option is disabled, users can manually download the payload by tapping the download button on the apparent video, as depicted in Figure 3.
When attempting to play the “video,” Telegram will display a message stating it cannot play the file and suggest using an external player (refer to Figure 4). This warning is authentic and sourced from Telegram’s legitimate codebase, not added by the malicious payload.
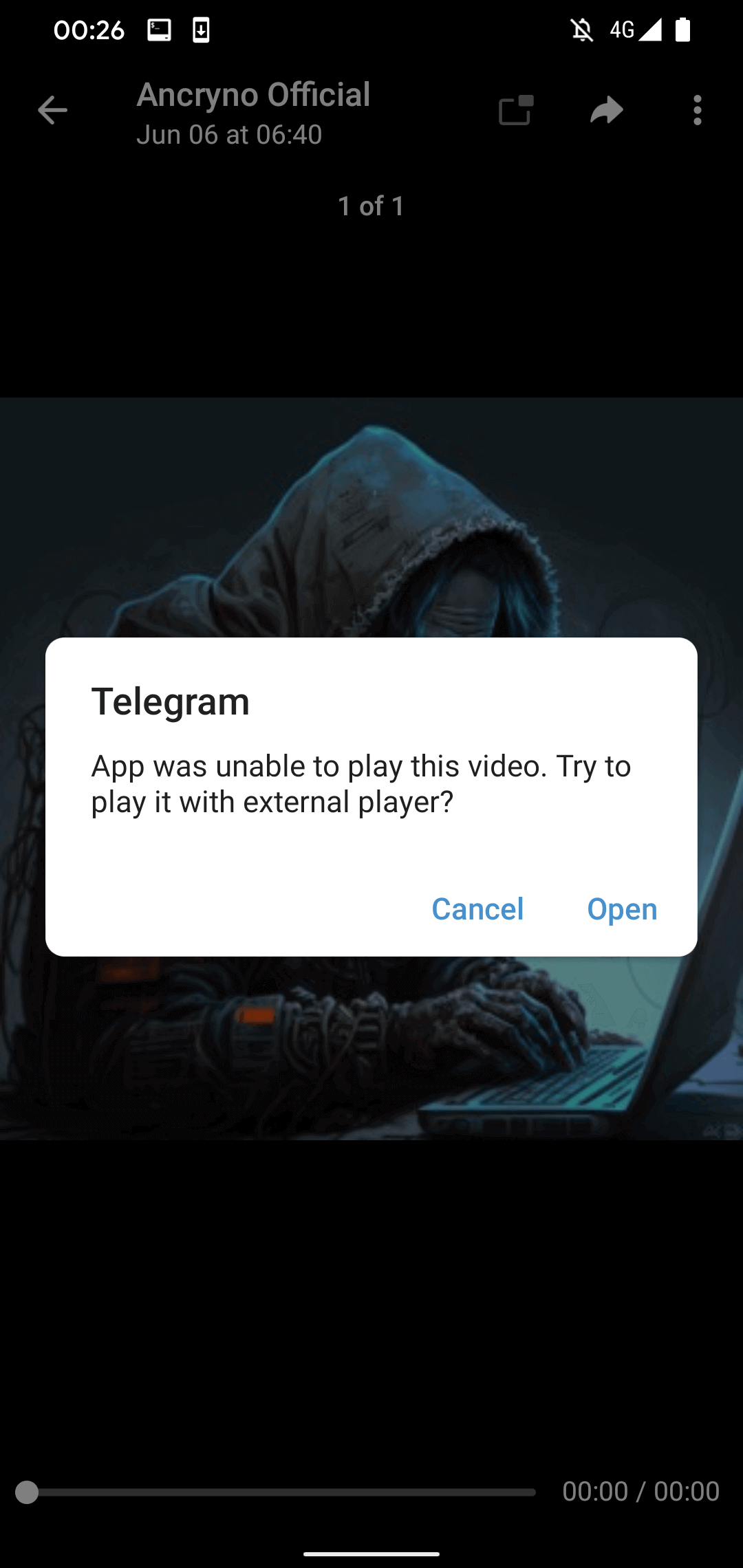
If users select the Open button in the message, they will be prompted to install a malicious app posing as an external player. As shown in Figure 5, this process requests enabling the installation of unknown apps.


